Every organisation is working remotely where multiple files are being shared through different kinds of sources every day and the best part is that different organisations are using a different kinds of tools in the whole process. All these kinds of activities are considered to be unavoidable because they are becoming a very important task to be undertaken to make sure that businesses can function very smoothly. Hence, in most organisations usernames and passwords are present in the database which is the main reason that people need to be aware of security-related guidelines in the whole process.
Whenever somebody will be attempting to log in to the system it will be checking the username and will be comparing the password entered by the user in the whole process so that everything will be undertaken successfully. Hence, it is very much important for the organisations to be clear about security at every level in the whole process so that overall goals are very easily achieved. Being very much clear about the implementation of the hashing algorithm is also very much important because this is the fundamental component of cryptography which will be based upon chopping the data into smaller parts so that it can be perfectly mixed up and will become very much difficult for the end-user to recognise it. The hedging function is considered to be the very Basic algorithm which will help in making sure that generation of the fixed-length result will be carried out very easily from the specific input data. This will be different from the very basic encryption system and will help in converting the normal system into a very safe and secured one so that overall goals are very easily achieved. If the organisations are interested to ensure top-notch password security then hashing will be very much capable of ensuring that passwords will be perfectly implemented by them and there will be no chance of any kind of problematic scenario in the whole process.
Which type of hashing function is a good one?
- Hashing functions should always be considered as one be a function because it will be impossible for people to go to the original text once it has been subjected to the hashing algorithm. So, if the organisations are interested to get a specific result then depending on the ideal function in this particular area is a good idea so that there is no chance of any kind of doubt.
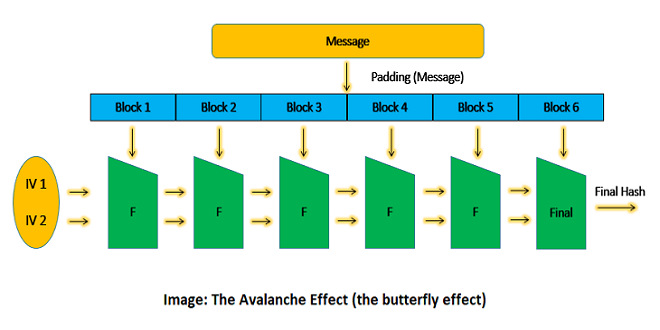
- It is very much important for the organisations to be clear about the avalanche effect in this particular case so that very minor changes in the inputs can be dealt with very easily without any kind of comprehensive changes in the output. A good function will always be one that will be using the avalanche effect very well and will be fulfilling different kinds of purposes very successfully.
- The organisations need to be clear about that particular type of function which is very fast in terms of computing and helps in making sure that overall goals are very easily achieved without things being strong in terms of implementation.
- One should always prefer that particular type of hashing function which does not have any kind of collision in terms of output and make sure that overall goals are very easily achieved.
- People need to depend on that particular type of function which is deterministic in the whole process it respective of the checking system which has been carried out over it.
It is very much important for people to be clear about the credentials element in the whole process because without implementation of the hashing algorithm in the place it could lead to different kinds of issues with the content and receiving part so that there is no chance of any kind of problem. But on the other hand, it is also very much important for the organisations to be clear about the different types, formats and number of attachments associated with the whole process to avoid any kind of chaos throughout the process. Different types of hashing algorithms available in the industry have been explained as follows:
- Message digest five: This is the most commonly used algorithm in the industry and whenever the password will be converted into a specific pattern with the help of this particular method it will be very easy to simply Google the hash value and get the original value in the whole process.
- SHA which is the secure hash algorithm family of algorithms: This is considered to be one of the most important improved versions of the earlier systems and has been perfectly used for the secure socket layer or SSL security so that overall goals are easily achieved. In this particular manner, the organisations will never be subject to different kinds of attacks in the whole process and everybody will be very much serious about the security concept.
- Whirlpool: This is the 512-bit hash function that has been developed with the help of advanced encryption standards so that overall goals are very easily achieved.
- RIPEMD family of algorithms: This is considered to be the perfect opportunity of ensuring the development of the things will be carried out very successfully and the output lens will be kept on increasing with the help of subsequent versions of the whole process. With the help of this particular aspect, the security coverage will be significantly increased without any kind of doubt element in the whole process.
- CRC32: This is considered to be the cyclic redundancy code which is known as one of the most important spreading properties in this particular case so that overall goals are very easily achieved and smooth file transfer, as well as validation, will be carried out in the whole process.
Hence, it is very much important for the organisations to be clear about the implementation of the right kind of hashing algorithms from the house of companies like Appsealing so that everything will be carried out very successfully and there will be no chance of any kind of problematic scenario in the whole process.
 TECHGUIDANCES
TECHGUIDANCES